Implementing SSO for Thinkific LMS using WSO2 Identity Server.

Thinkific is a software platform that enables entrepreneurs to create, market, sell, and deliver their own online courses. Besides that, if you’re having multiple applications on your organization and if you want to implement a single point of authentication platform (Single Sign-On) for your users including the Thinkific LMS, WSO2 Identity Server provides it acting as an Identity Provider. Put differently, WSO2 Identity Server provides the capability of implementing SSO for Thinkific LMS which lets the users sign in to Thinkific LMS in a similar way the users sign in to other applications.
Wanna understand how it works?
Let’s start configuring the LMS
There is nothing specifically to configure on the Thinkific LMS except customizing the UI. Let’s customize the UI in the latter part of this article.
For now, let’s get the configuration details from LMS to integrate LMS with WSO2 Identity Server by signing into the admin portal of Thinkific LMS. Take a note of the below and we’ll be using it when we configure the Service Provider in the WSO2 Identity Server.
1. Site URL
The site URL of your Thinkific application can be found at Settings ➜ Site ➜ Site URL section in the admin portal. It will look something like below.
https://your-school.thinkific.com
Otherwise, there will be a custom site URL if you have configured a custom site URL for your Thinkific LMS.
2. API Key
The API Key of your Thinkific application can be found at Settings ➜ Code & analytics ➜ API section in the admin portal.
Let’s configure WSO2 Identity Server
It’s time to get WSO2 Identity Server 5.10 if you haven’t done yet.
Get the connector from the WSO2 IS connector store.
Let’s download the jar file and place it inside the below directory.
<IS_HOME>/repository/components/dropinsAdd the configuration below in deployment.toml file resides in <IS_HOME>/repository/conf directory and start the server (restart if the server is already up and running).
[[resource.access_control]]
context="/identity(.*)"
secure="false"
http_method="GET"
If you’re new to WSO2 Identity Server, you may refer below to run the product.
Once the server is up and running, access the management console at https://localhost:9443/carbon and login with the admin credentials (The default credentials would be admin:admin).
Let’s configure the service provider as depicted below.
Navigate to Main ➜ Service Providers ➜ Add and register a new service provider in the WSO2 IS management console.
Then navigate to Inbound Authentication Configuration ➜ JWT SSO Configuration. The JWT SSO Configuration is the one we’ve added newly by placing the jar in the dropins directory.
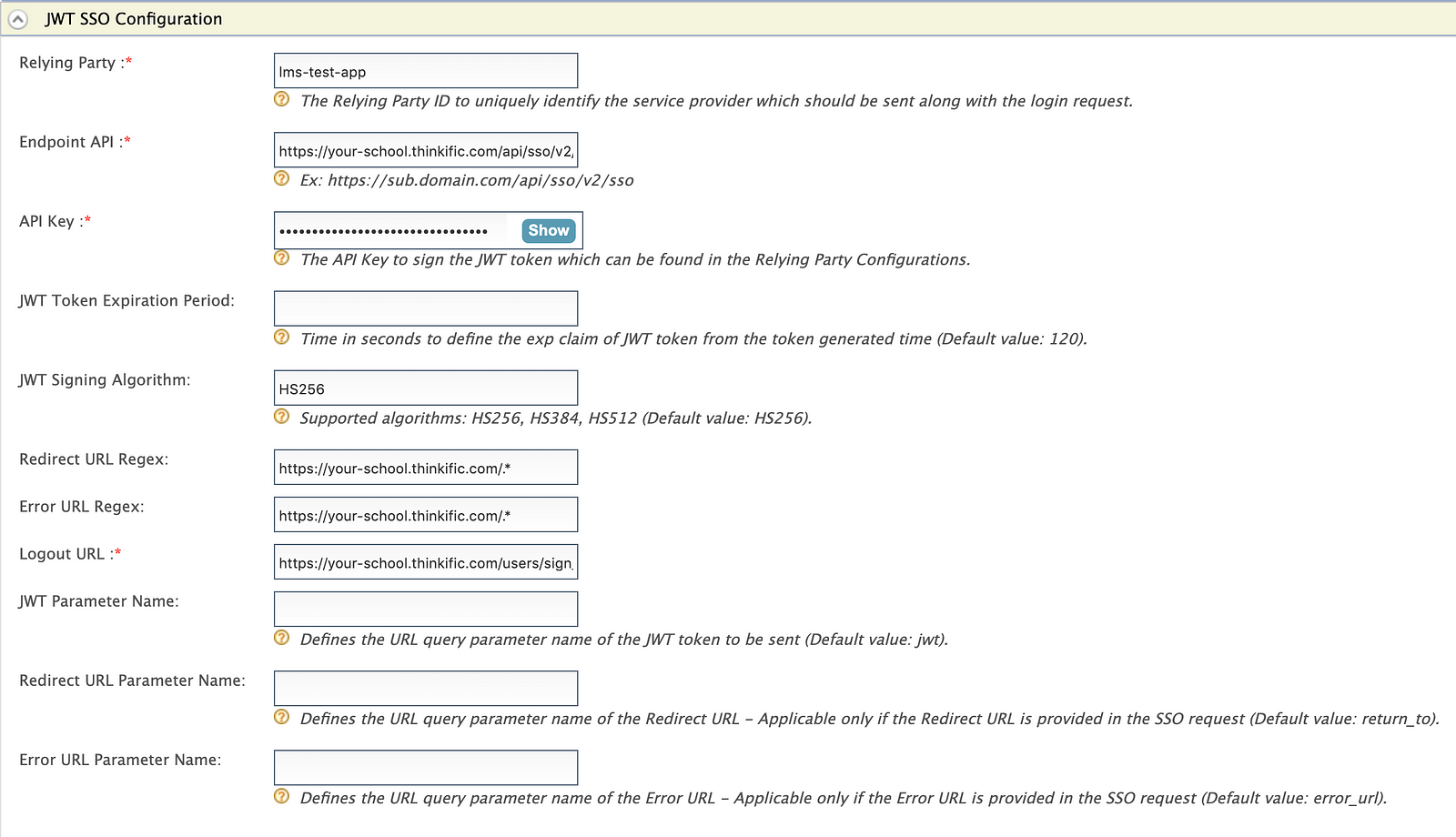
Enter lms-test-app for Relying Party and enter the Endpoint API and the API Key which we’ve obtained from Thinkific LMS.
The below table describes the properties used in the JWT SSO inbound authenticator and the sample values related to those properties.
Regarding the Logout URL, the Thinkific LMS does not have a logout endpoint to terminate the particular user’s session by sending the user session identifier, instead, it has the logout URL which should be invoked through the browser which will terminate the user session based on the cookies sent along with the request.
Therefore, in this scenario, when the user clicks on the Sign-out button of LMS, the logout request will be sent to WSO2 IS and it’ll terminate the session on exists on the WSO2 IS. Once the user session is terminated on the WSO2 IS, it will make a redirection call to the Logout URL specified and hence the LMS session will also be terminated.
Once you've completed configuring the JWT SSO configuration, we have to configure the claims required by Thinkific LMS to create and identify the user. As per the Thinkific Documentation, the below claims are supported by Thinkific LMS.
- email (required) — the email of the authenticated user. If external_id is not supplied, email will be used as the unique identifier.
- first_name (required)- the first name of the authenticated user.
- last_name (required)- the last name of the authenticated user.
- iat (required) — must be the number of seconds since UNIX epoch. This is essentially the time that the JWT payload was issued.
- external_id — an identifier for the authenticated user. This is typically the id of the user in your system. This is OPTIONAL, but if supplied will be used as the unique identifier of the user. What this means is that when your student is trying to log in and you have included external_id in the payload, the Thinkific database will look for a user with that external_id. If that user is not found, the system will attempt to create them.
- bio — a textual bio of the user. This is OPTIONAL.
- company — the user’s company. This is OPTIONAL.
- timezone — the user’s timezone abbreviation (as defined here: https://www.iana.org/time-zones). This is OPTIONAL.
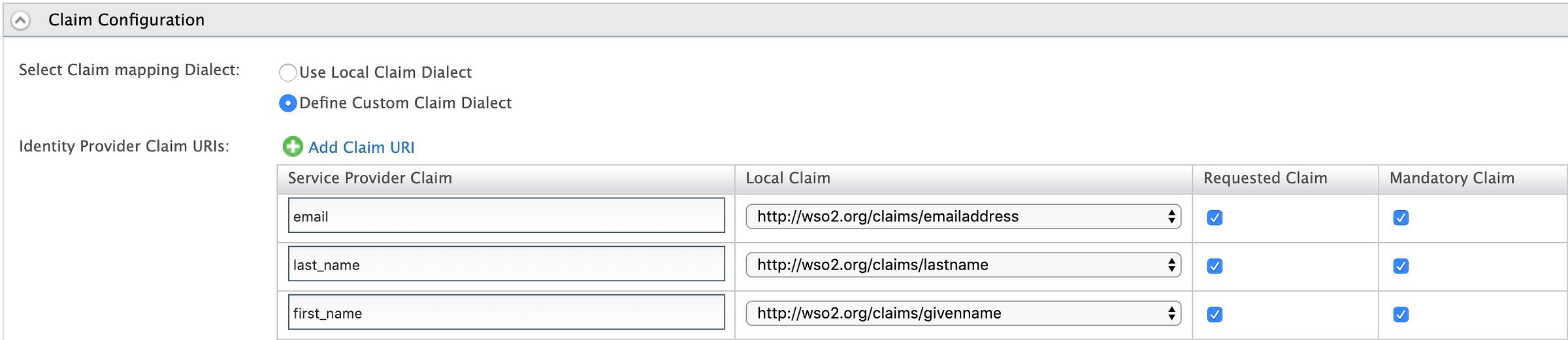
Let’s configure the mandatory claims in the WSO2 Identity Server SP claims configuration as follows.
- Navigate to the Service Provider you’ve created earlier and expand the Claim Configuration section.
- Select Define Custom Claim Dialect as the Claim mapping Dialect.
- Define the Service Provider Claims (as required by Thinkific LMS) and the related Local Claims (Claims available in WSO2 Identity Server) as below. (This is required to include the user claims in the JWT token; otherwise, no attributes will be included in the JWT token apart from the default attributes such as exp and iat.) Also, mark those claims as Requested Claim and Mandatory Claim so that the user will be prompted to add the claim value if it is not set for the particular user.
That’s! We’re good to start testing the configurations before we do the customizations on Thinkific LMS.
Let’s make an authentication request to WSO2 Identity Server as follows.
https://localhost:9443/identity/jwtsso?jwtRP=lms-test-appNow you should be prompted with the login page of WSO2 Identity Server if you’re not already authenticated and once you’re authenticated, you should directly be redirected to the Thinkific LMS without prompting the Login page of Thinkific. Further, if you do not have an account on Thinkific LMS, an account will be created for you (user will be provisioned) by Thinkific LMS with the claim values we’ve configured above.
Let’s test the logout flow by making the request as follows.
https://localhost:9443/identity/jwtsso/logout?jwtRP=lms-test-appOnce you make the above request, your session should be terminated from WSO2 Identity Server as well as from the Thinkific LMS. You can verify whether your session on WSO2 Identity Server is terminated by making the authentication request again and you should be prompted with the login page of WSO2 Identity Server if the session is terminated successfully.
If all goes well, we’re good to start customizing the Thinkific LMS theme to redirect the users to WSO2 Identity Server for authentication.
If you got any error message in Thinkific LMS after the successful authentication in WSO2 Identity Server, there is a high chance you haven’t configured the claims properly in the claim configuration section of the service provider. However, if you got any errors in WSO2 Identity Server during the authentication process, you’ll have to refer to the below section too!
Having any issues? Let’s debug!
If you got any error while testing the flow, an error log or an exception should be logged in the wso2carbon log which will help you identify the cause for the issue. If you’re running the server as a background process or as a system service, you may have a look at the wso2carbon log file as follows.
tail -f <IS_HOME>/repository/logs/wso2carbon.logHowever, if you’re still unclear on the error, we may dig a little deeper into the flow of the authentication process by enabling the debug level logs.
1. Add the below lines in the log4j2.properties file resides in <IS_HOME>/repository/conf directory.
2. Append the org-wso2-carbon-identity-sso-jwt to loggers variable as follows.
That’s it! The loggers will be updated in the runtime (Restart is not required) and you’ll see the debug level logs printing in the wso2carbon log when you try the flow again. I believe it’ll help you find the cause of the issue.
Let’s customize the Thinkific LMS
Let’s customize the Thinkific LMS sign-in and sign-up buttons to redirect the users to WSO2 Identity Server for authentication. Before we dig into the customization on a production setup of Thinkific LMS, I’d recommend contacting Thinkific LMS support if you have any concerns or clarifications.
You can learn more about Thinkific LMS customization on the Thinkific developer documentation below.
The customization explained below focuses on the Empire theme of Thinkific LMS.
- Navigate to snippets directory and open the meta_tags.liquid file.
- Navigate to following sections and add the simple javascript codes as below to implement the redirect.
To be honest, I haven’t tested the Thinkific LMS customization yet.
If all goes well, we’re done integrating Thinkific LMS with WSO2 Identity Server!
Cheers!
